CALL 1300 654 201 | GENUINE HID GOLD PARTNER


Future-Proof Your Organisation
Organisations often struggle to merge end-user needs and IT requirements into a budget-friendly, single Zero Trust product that is easy to implement. While users need access to a variety of IT resources conveniently and efficiently, IT requires that the entire environment is secured, from physical entry to IT systems to cloud apps.
HID Crescendo® Smart Cards and Security Keys Rise to the Challenge
When HID Crescendo® is combined with our identity lifecycle management solution, organisations can automate provisioning and de-provisioning of credentials and digital certificates with flexibility and scalability as they grow.
HID® Crescendo® C2300 Smart Card Series
HID® Crescendo® Key Series


Converged Credential Ecosystem
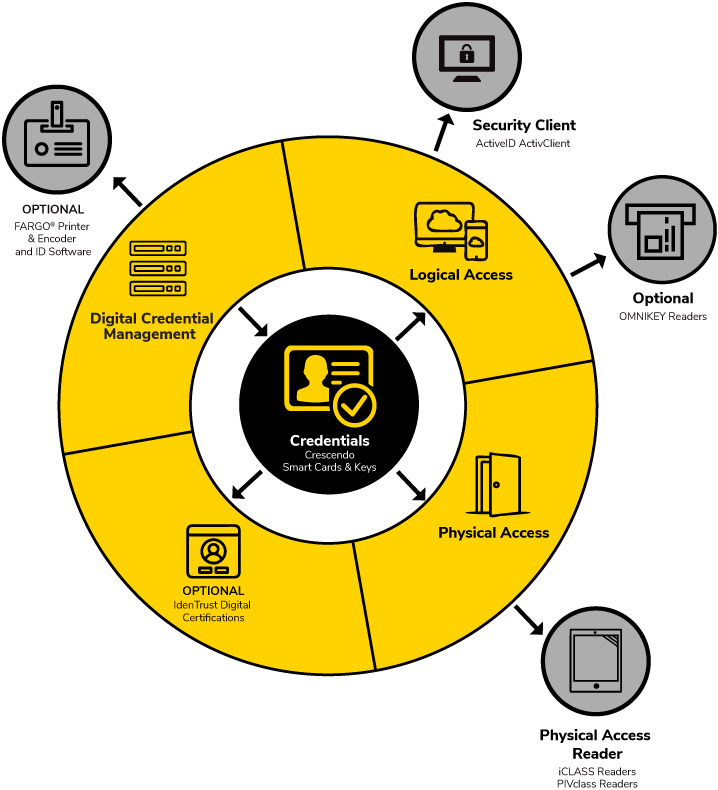

One Authenticator, Many Uses
Secure access to IT applications, networks and systems
like Virtual Private Networks, and Microsoft Active Directory and Azure Active Directory.
Secure access to web and cloud applications
such as G Suite, Dropbox, etc.
Secure access to premises
with a converged corporate badge (including with Seos®) that can also be used to access IT applications.
Protect communication and data
with public key certificates, by digitally signing and encrypting emails, and by encrypting data at rest.
Digitally sign documents
ensuring they have not been tampered with and confirming their provenance.
Provide secure printing
ensuring that a sensitive document is only released from the printer after the user is authenticated at the printer.



